Domain Name System (DNS) Internet Protocol packets use IP addresses rather than names:
- Designed for efficient processing by routers determining where to forward the packet
- Not human readable - people prefer names, not addresses
DNS Queries are generally made over UDP port 53
DNS therefore is a distributed database that maps names to IP addresses
for example:
URL: https://www.csperkins.org/teaching
⇒ Domain Name: www.csperkins.org
⇒ DNS
⇒ IPv4: 93.93.131.127, IPv6: 2a00:1098:0:86:1000::10
DNS is structured heirarchically:
www . csperkins . org [ ] ← (DNS Root) | | | Subdomains | | Top-Level Domain
Concludes with a top-level domain (TLD)
- Country-code top-level domains (ccTLDs)
- .uk, .de, .cn, .io, .ly, …
- Generic top-level domains (gTLDs)
- .com, .org, .net, …
- Top-level domains live within the DNS root
- The root servers advertise the top-level domains
- They have well-known, fixed, IP addresses – new DNS resolvers need to reach them to find the TLDs before they can answer DNS queries
Each level is independently administered and operated
- DNS is a distributed database – in authority and implementation
- Each level in the hierarchy controls its own data
DNS Resolution
The DNS is used for name resolution
- Given a name, lookup a particular type of record relating to that name
- Many different types of record: A, AAAA, CNAME, MX, NS, SRV, …
- Most common are A and AAAA records, that map hostnames to IPv4 and IPv6 addresses, and NS records that identify the name server for a domain
- NS - IP of Name Servers
- CNAME - Canonical names, aliases in the DNS
- MX - Mail Exchange
- SRV - Generalised Server Lookup
A DNS client asks its resolver to perform the lookup by calling getaddrinfo()
The resolver could be a process running on the client, it more commonly runs on a machine provided by the network operator.
DNS Resolvers
When connecting to network, hosts use DHCP (dynamic host configuration protocol) to discover network settings and configuration
- DHCP tells the host what DNS resolver to use for the network
- If a host has multiple network interfaces, it may use a different DNS resolver for each
- The
getaddrinfo()call takes a hints parameter, that can include the local IP address - e.g., consider a device connected to 4G cellular network and a private company Ethernet – the Ethernet might make available names of internal services that aren’t accessible to the public
- The
Possible to configure the DNS resolver manually e.g., to talk to Google public DNS resolver (IPv4 address 8.8.8.8)
For a long time, DNS resolution has typically been a system-wide service, where an OS implements a DNS resolution service, and we use that. DoH is changing this
- Much easier to perform their own DNS queries
- Giving applications ability to securely access arbitrary DNS servers allows them to avoid local observation and/or filtering of DNS traffic
Is this flexibility for each application to perform DNS queries differently a concern? Yes
- Network operators filter DNS responses to block access to malicious sites and prevent malware spreading – allowing applications to bypass this is a security risk
- Network operators filter DNS responses to enforce legal or societal constraints – e.g., Internet Watch Foundation DNS block list to stop UK-based access to sites hosting child sexual abuse material No
- Applications should have the ability to use a secure DNS server they trust to avoid phishing attacks, malware, monitoring, etc.
- Why should network operators be able to see DNS queries and modify responses? This is a privacy and security risk
TTL
All responses contain a Time To Live that allows the resolver to cache the value for a certain amount of time.
Subdomains can set a short TTL and give different answers each time a particular name is requested → load balancing; CDNs directing queries to local caches
The IP addresses for the root servers are well known, and never time out
Example
Here are the DNS queries made by a resolver with no prior information when asked
What is the A record for www.csperkins.org
- What is the NS record for
.org? (DNS Root Servers) - What is the NS record for
.csperkins.org? (.org Servers/ TLD servers) - What is the A record for
www.csperkins.org? (.cspekins.org server)
Top Level Domains
ICANN controls the set of Top Level Domains
gTLDs : Generic Name Supporting Organisation
- Core Set:
- .com, .org, .net - unrestricted use (company, not profit org, network)
- .edu - higher education, restricted use, mainly
- .mil - US military
- .gov - US gov
- .int - international treaty orgs
- ICANN has since massively expanded the set of gTLDs:
- 1500 gTLDs
ccTLDs: Country Code Name Supporting Organisation
Matches ISO standard 3166-1
Exceptions:
.gb, the UK should technically use .gb.su, the domain for the soviet union still exists and accepts registration.euthe EU is not a country, but has a ccTLD.ozsadly Australia changed from.ozto.au
- 1500 gTLDs
ccTLDs: Country Code Name Supporting Organisation
Matches ISO standard 3166-1
Exceptions:
Infrastructure top-level domains
- .arpa - mainly historical, useful however for reverse DNS
- To look up
93.93.131.127for example, you search:127.131.93.93.in-addr.arpawill returncsperkins.org - For
2a00:1098:0:86:1000::10you search0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.1.0.0.6.8.0.0.0.0.8.9.0.1.0.0.a.2.in6.arpa
- To look up
Special Use top-level domains
- .example - examples and documentation (example.com, etc exist as well)
- .invalid - guaranteed to never exist
- .local - local network
- .localhost - local machine
- .onion - gateway to TOR network
- .test
International DNS
Internationalised DNS works around this by translating non-ASCII names into ASCII: Punycode:
- Encodes any unicode text as a sequence of ASCII letters, digits, and hyphens
- München → Mnchen-3ya
- Bahnhof München-Ost → Bahnhof Mnchen-Ost-u6b
- Part after final hyphen is a base-36 (a-z0-9) encoded representation of a sequence of Unicode character and the locations where they should be inserted
Internationalised DNS names use Punycode, prefixed with xn-- • e.g., http://Яндекс.рф translates to http://xn—70akdum1a.xn—p1ai (Yandex, a Russian search engine)
xn— was used as it didnt exist in any top level domain
DNS Root
What are the root servers?
The set of 13 servers that advertise the name servers for the top level domains
- a.root-servers.net → m.root-servers.net
- Also have well-known IPv4 and IPv6 addresses
Why 13 servers?
- Want to be able to ask a DNS resolver to return a list of the root servers
- DNS over UDP has a size limit on relies → 13 root servers is all that will fit into a single UDP packet
There aren’t 13 PHYSICAL Servers: Anycast Routing - i.e. same IP used for many places in the network
Security
Historically DNS has been completely insecure Trivial to eavesdrop, forge replies
Two approaches to secure DNS:
Can block DNS-over-UDP by blocking UDP port 53,
and block DNS-over-TLS by blocking TCP port 853,
DNS-over-HTTPS is much harder
- Encrypted, however you can tell the common ones like googles IPv4:
8.8.8.8
Transport Security:
- Make DNS requests, and receive replies, over TLS (or some other secure channel)
- Requests are responses are encrypted, so can’t be understood or modified by attacker
- If you trust the resolver, this protects against attack
Record Security:
- Add a digital signature to DNS responses that client can verify to check the data is valid
- ICANN signs the root zone
- Root servers sign information they provide about TLDs
- TLDs sign information they provide about sub-domains
DNS over TLS
Structure:
- DNS client opens a TCP connection to the resolver (port 853)
- DNS client and resolver negotiate a TLS 1.3 session on the TCP connection
- DNS client sends query, and receives response, over the TLS connection
- DNS over TLS messages are formatted exactly the same as DNS over UDP, and contain exactly the same information – only difference is that they’re sent over TLS not UDP
- Slower and higher overhead than DNS over UDP – due to need to negotiate TCP and TLS –but more secure
DNS over QUIC (DoQ)
Fundamentally same concept as DNS over TLS, with less overhead
DNS over HTTPS (DoH)
DoH allows a client to send queries to a resolver using HTTPS -
- Can use with either GET or POST methods in HTTPS
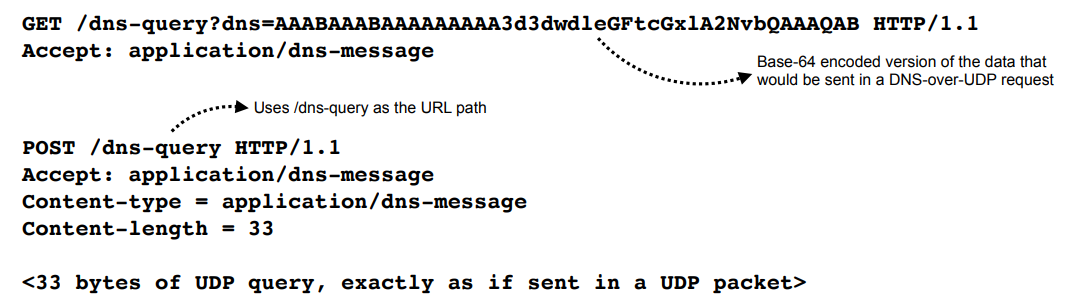
- HTTP response has Content-Type:
application/dns-messageand contains the exact same data that would be sent in a UDP-based DNS response
Packet Structure
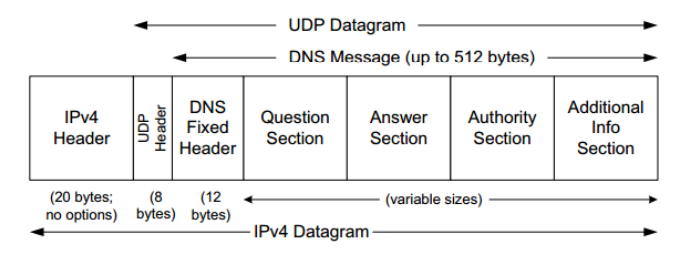
The DNS message of:
- DNS Fixed Header (Fixed 12 Byte)
- Question Section - e.g. what is
AAAArecord of domaincsperkins.org, can be more than one - Answer Section - Responds with IP, as well as the TTL
- Authority Section - Responds with authority
- Additional Info Section Stored inside the UDP Datagram Stored inside the IPv4 Datagram