OS-assisted virtualization, also known as paravirtualization, is a virtualization technique where the guest operating system is modified to be aware that it is running in a virtualized environment. This approach allows the guest OS to cooperate with the hypervisor to achieve better performance than full virtualization, especially on architectures that don’t perfectly satisfy Popek and Goldberg’s Theorem.
Key Concept
The fundamental idea of OS-assisted virtualization is to:
Make the guest OS aware that it is being virtualized and modify it to directly communicate with the hypervisor, avoiding the need for complex techniques like binary translation or hardware extensions.
How OS-Assisted Virtualization Works
- The guest OS is modified to replace non-virtualizable instructions with explicit calls to the hypervisor (hypercalls)
- The guest OS is aware it doesn’t have direct access to physical hardware
- The hypervisor provides an API that the modified guest OS uses for privileged operations
- The guest still maintains its device drivers, memory management, and process scheduling, but in coordination with the hypervisor
Xen: A Classic Example
Xen is the most well-known example of OS-assisted virtualization:
Xen Architecture
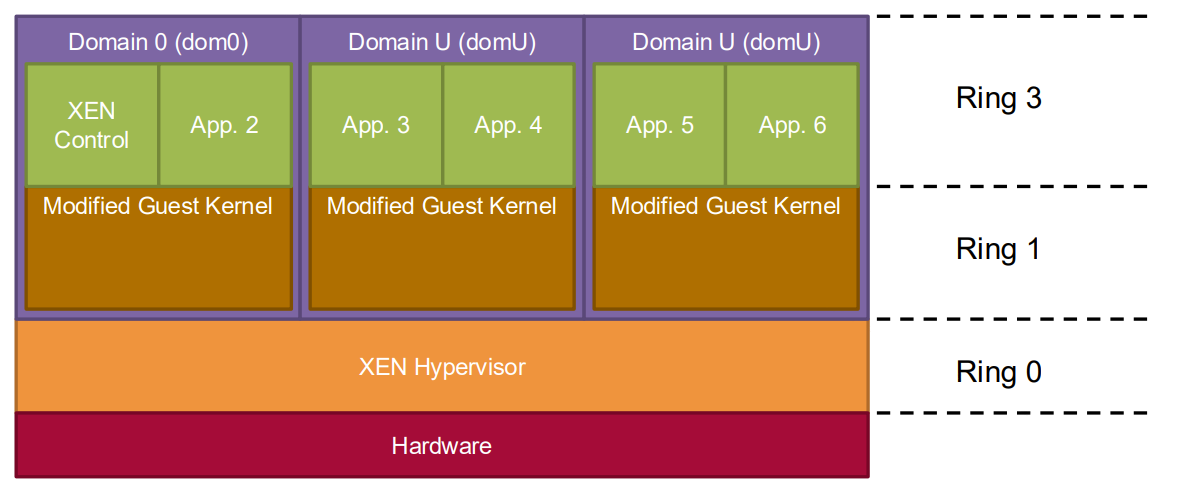
- Hypervisor: A thin layer running directly on hardware (Type 1)
- Domain 0 (dom0): Privileged guest for control and management
- Domain U (domU): Unprivileged guest domains with Xen-aware OS
Xen uses a ring structure for privileges:
- Hypervisor runs in Ring 0 (most privileged)
- Guest OS kernels run in Ring 1
- Guest applications run in Ring 3 (least privileged)
CPU Virtualization in Xen
- Guest OS is modified to run in Ring 1 instead of Ring 0
- Critical instructions are replaced with hypercalls
- Hypercalls are explicit calls from the guest OS to the hypervisor
- System calls from applications to the guest OS can sometimes bypass the hypervisor for better performance
Memory Management in Xen
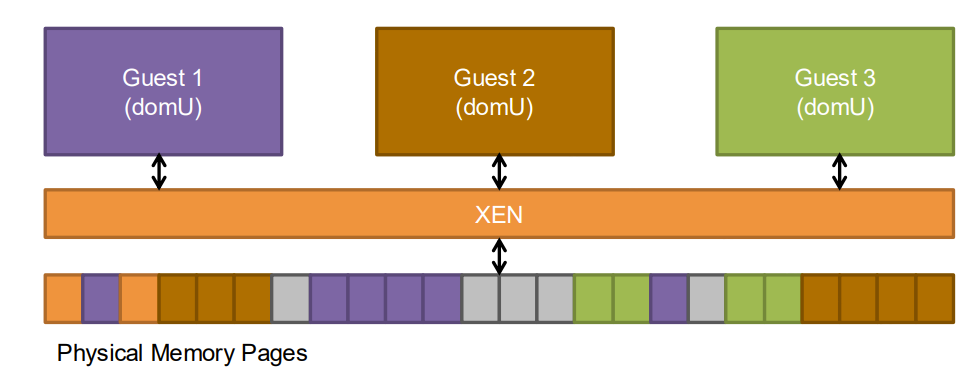
Xen’s approach to memory management is distinctive:
- Physical memory is statically partitioned among domains at creation time
- Each domain is aware of its physical memory allocation
- Domains maintain their own page tables, validated by the hypervisor
- The guest page tables are used directly by the hardware MMU
- Updates to page tables require hypervisor validation to ensure isolation
- No shadow page tables are needed (unlike in Full Virtualization)
I/O Virtualization in Xen
Xen provides virtual devices through a split-driver model:
- Front-end drivers in guest domains (domU)
- Back-end drivers in the privileged domain (dom0)
- Communication through shared memory and event channels
- Physical device drivers reside in dom0
Performance Advantages
OS-assisted virtualization offers several performance advantages:
- No need for binary translation or instruction emulation
- Direct memory management without shadow page tables
- More efficient I/O through paravirtualized drivers
- Reduced context switching overhead
- Explicit cooperation between guest and hypervisor
Limitations
Despite its performance benefits, OS-assisted virtualization has limitations:
- Requires guest OS modifications: Source code access and modification is necessary
- Limited OS support: Only OSes that have been specifically modified can run
- Maintenance burden: Modified OSes must be maintained separately from mainline versions
- Porting effort: Each new OS version requires porting effort
Comparison with Other Approaches
When compared to other virtualization techniques:
- vs. Full Virtualization: Better performance but requires OS modifications
- vs. Hardware-Assisted Virtualization: Similar performance in some cases, but doesn’t require specialized hardware