External BGP (eBGP)
External BGP (eBGP) used to exchange routing information between ASes
- An eBGP session is used by an AS to exchange information about the AS-level topology with a neighbouring AS
- Runs over a TCP connection between two routers, one in each AS
- Exchanges knowledge of the AS-level topology of the network, filtered according to policy
- Used to compute appropriate interdomain routes to each destination AS
Routing Tables
Each eBGP router advertise a list of IP address ranges (“prefixes”) and their associated AS-level paths This all gets combined into a routing table
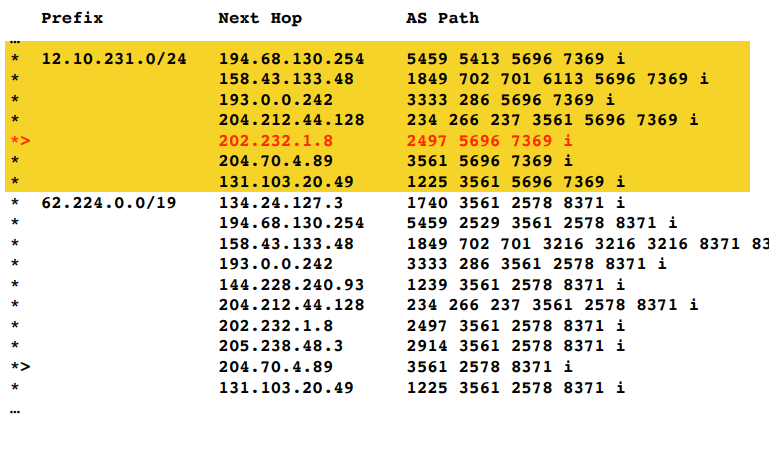
- Hosts with IP addresses in the range 12.10.231.0 - 12.10.231.255 are in AS 7369.
- That AS is best reached via AS 2497, then AS 5696.
- Packets destined for those addresses should be sent to address 202.232.1.8 next, from where they will be forwarded.
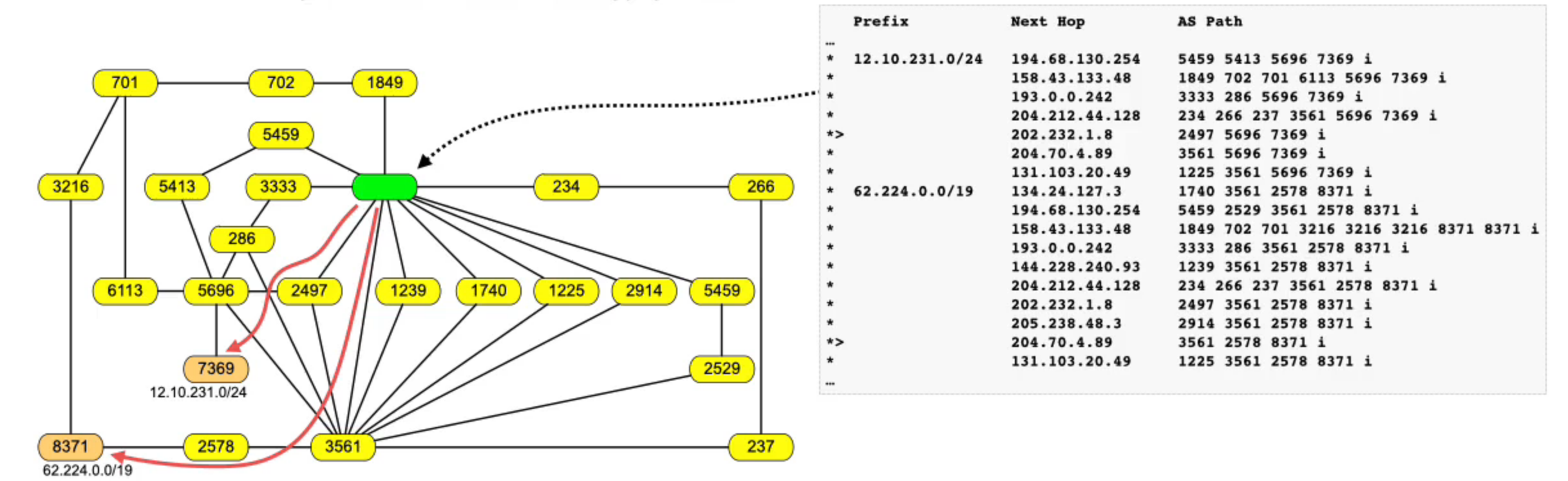
AS Topology from Routing Tables
Routing Policy
Each AS chooses what routes to advertise to its neighbours
- Doesn’t need to advertise everything it receives Usual to drop some routes from the advertisement – depends on the chosen routing policy
Generally:
Gao-Rexford Rule
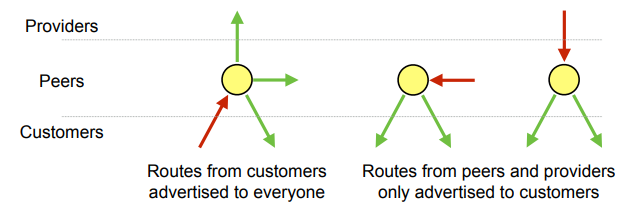 Gao-Rexford rules specify what routes are advertised, not how traffic is forwarded – difference between control plane and data plane
Gao-Rexford rules specify what routes are advertised, not how traffic is forwarded – difference between control plane and data plane
- Resulting graph is valley-free DAG: traffic flows up to common provider, then down
- Designed to optimise profit, not routing efficiency – don’t advertise expensive routes
Each AS:
- Exchanges routing information with neighbours
- AS-level topology information, filtered based on policies applied by each AS
- Gives a partial view of AS-level network topology
- Applies policy to choose what routes to use:
- Choose what route to install in forwarding table for each destination prefix
- BGP may not find a route, even if one exists, since may be prohibited by policy
- Routes are often not the shortest AS path – shortest policy-compliant path
- Applies policy to determine what routes to advertise to neighbours
- Filter out routes the neighbour should not use (e.g., Gao-Rexford rules, and other reasons)
- De-prioritise certain other routes
- Tag routes for special processing where business agreements exist
- Mapping business goals to BGP policies is poorly documented → many operational secrets
Simplified BGP decision process
# | Criteria
----------------------------------------------------------
1 | Highest LocalPref
2 | Lowest AS Path Length
3 | Lowest origin type
4 | Lowest MED
5 | eBGP-learned over iBGP-learned
6 | Lowest IGP cost to border router (hot-potato routing)
7 | If both paths are external, prefer the oldest path
8 | Lowest router ID (to break ties)
Internal BGP (iBGP)
- An Intra-Domain Routing protocol determines routes within the AS
- iBGP distributes information to internal routers on how to reach external destinations
BGP Hijacking
Any AS participating in BGP routing can announce any address prefix – whether or not they own it
- Sometimes this is accidental
- Sometimes this is malicious
Result is that traffic is misdirected: BGP hijacking
- Security risk if traffic can be misdirected
- Accidental hijacking is a serious stability problem for the network
Solution?
Resource Public Key Infrastructure (RPKI)
RPKI is an attempt to secure Internet routing
- Lets an AS make a signed Route Origin Authorisation (ROA) – a digital signature, announced via BGP, proving the AS is authorised to announce a IP address prefix
- Hierarchical delegation: RIR → provider AS → customer AS
- Allows a router to validate whether a prefix announcement is authorised – hijacked prefixes will not have a valid signature
- Becomes part of BGP policy: prefer signed prefixes